12 Most Notorious & Biggest Cyberattack in History

A cyberattack is an unauthorized interference by which data can be stolen without showing body or face. Nowadays people are performing on the digital platform and millions of data are stored in the server. In that case, there is a great chance to steal data from the server by unauthorized interference. We know that the world has witnessed many notorious and biggest cyberattack in history such as the Ukraine power grid attack, the Estonia Cyber Attack, the NASA Cyber Attack, etc. But how do cyber criminals do it? Let’s see the 12 most notorious & biggest cyberattack in history and find the details.
What is a Cyberattack?
A cyberattack is an unauthorized interference to your computer network to steal data. There are different types of cyberattack, such as Malware in cyber security, Ransomware, Domain name systems (DNS), password attacks, and others. Each thing has a specific attacking strategy. Indeed, an attacker is a person who conducts a cyberattack. This person is called a cybercriminal.
However, this attack is well well-known and unexpected. To get rid of such a brutal attack a well and smart cybersecurity system is required. In most cases, a question appears in our mind: what does cyber warfare mean? Cyber warfare means cyber war that conducts to cripple a country (economy, fighting weapons, etc.). Nowadays most powerful countries have emphasized that.
Biggest Cyberattack in History (Most 12 Notorious Attacks)

Cybercrime is not a new threat or crime. The world has faced a mega cyberattack several times. The first cyber attack occurred in 1834 in France. From then, the world has been witness to more than hundred times for small, medium, and biggest hack.
Cyberattack can destroy business growth. There are different ways to attack or steal data from a server. However, let’s see what was the biggest hack in cybersecurity history or how the biggest cyberattack was conducted in history.
#1. Estonia Cyber Attack in 2007
Estonia is a north European country. In April 2007 Estonia faced a brutal cyberattack that is never forgettable. It can be considered as the biggest hacks in history. Estonia faced a series of attacks. This attack was included in vast areas, such as the Estonian parliament, banks, ministries, newspapers, and broadcasters.
It lasted for more than a week. Why did this attack happen? Whenever the Estonian government decided to move the bronze soldier or soviet troops Tallinn centers to a less-priority military community that is located on the outskirts of the city.
The Estonian government estimated that Russia conducted this attack. During this attack, more than 58 essential Estonian websites were offline. This attack was caused by the distributed denial-of-service (DDoS) attack which overloaded the Estonian server.
#2. Cyberattack in Iran Uranium Plant in 2010
Stuxnet Cyberattack was conducted on the Iran uranium plant. It is one of the most dangerous hacking. Stuxnet is a harmful computer worm first discovered in 2010. Stuxnet malware motive to any other usual cyberattack.
This malware gives access to the hackers in successful computer control. It was conducted in the Iran uranium plant which is considered as the biggest cyberattack on any uranium field. Stuxnet came with its deadly face and almost damaged all the nuclear infrastructure.
It has taken control of more than 200000 computers in a nuclear enrichment plant and 14 industrial sites. Iran's targeted Stuxnet was spread by Siemens industrial control system and Microsoft Windows. It largely damaged the uranium reactor centrifuge.
This was the greatest cyberattack or cyber weapon. At last, Iran found the cybercriminals (The USA and Israel). It was the first successful cyber mission on behalf of the USA and Israel. But there is no clear evidence for that. The USA and Israel have made Stuxnet to control Iran's progress in the nuclear era.
#3. Cyberattack on Ukrainian Power Grid in 2015
Another unprecedented cyberattack was conducted on the Ukrainian Power Grid in December 2015. It was the worst cyber attack in history. During that time several parts of Ukraine had power outages. It was not a general blackout. This blackout occurred due to a Cyberattack on the Ukrainian power grid. It was the first and biggest cyberattack in history on the power grid. Indeed it was a phishing hack.
At first, hackers sent phishing emails to the power companies. And they get access by email exchange. By attacking the power grid 30 high-voltage electrical substations were blacked out. 230000 people were deprived of electricity for 1 to 6 hours. A US investigator team found some issues and was responsible to the Russian hackers for that. US experts warned others to save themselves from such a brutal cyberattack.
#4. NASA Cyberattack in 1999
NASA cyberattack is another world's largest cyberattack in history. It was held in 1999. This attack caused the shutdown of NASA computers for 21 days. The first attack was conducted in 1971 to test their security system. The main reason for hackers is to steal data from NASA computers or data centers.
During this period, hackers downloaded 1.7 million pieces of software which cost around $41000 to repair. But who was responsible for that? “Jonathon James” was responsible for that. He was a 15-year-old hacker who occupied a NASA computer access using a computer operating system and kept such computers in his control for more than half a month.
However, how many times has NASA suffered from a cyberattack? NASA's chief information officer said they have faced more than 6000 times of various types of cyber hacking over the past 4 years. But they have been working to improve their security system and save them from notorious Cybercrime.
#5. Sony Pictures Hack in 2014
Another biggest cyber attack in history is to hack Sony Pictures. Sony is a giant multiplatform company in the digital platform. Sony became a victim of hacking in 2014. During this attack, hackers identified their groups as ‘’Guardians of Peace’’ and they leaked a bunch of crucial data from Sony film studio or Sony Pictures Entertainment (SPE).
These stolen data include Sony Pictures employee's personal information, company information, copy of unreleased Sony films, and other data. The hackers have taken 100 terabytes of data from Sony.
Why did hackers hack Sony pictures? They were hacked to withdraw Sony's upcoming film “The Interview”. However, the US investigator said that who was responsible for this cyberattack is undefined. However, most experts suspect North Korean hackers because it was a comedy film and related to the North Korean Government.
#6. Cyberattack in US TJX Retailer Company in 2006
TJX is a giant US retailer company. In December 2006 TJX was the victim of a cyberattack. During this attack, hackers stole 45.6 million debit and credit card data. It has happened in one of its systems over 18 months. It is the biggest cyberattack in history to steal personal data. Who was the mastermind of this attack? “Albert Gonzalez” is an American hacker and he was responsible for this situation.
However, many of the customers pick the question about the TJX customer data protection system. TJX retail company hack has a high impact on the retail industry. From then TJX became serious about the customer data protection system and cybercrime.
#7. Home Depot's Cyberattack in 2014
Home Depot is the largest home improvement retailer company in the United States. It was the victim of a cyberattack in 2014. There were millions of customer data stored in their history. The Home Depot reached a $17.5 million settlement over the 2014 data breach. Reuters says hackers have stolen 40 million customer data (payment card data) and 52 million email addresses.
In that case, cybercriminals used third-party vendors ' names and passwords to enter the Home Depot network. They also check the US and Canadian systems. Due to the low security, hackers entered to steal the data. After that occurrence, Home Depot hardly worked to make their server and security system not happen again in the next.
#8. WannaCry Ransomware Attack in 2017
The WannaCry Ransomware Attack was the world's deadliest cyberattack in the world. It was the most popular ransomware in history. This attack was conducted on Microsoft Windows operating system installed computers by locking computer data. It was held in 2017 and impacted more than 200,000 computers in over 150 countries.
The attackers targeted some giant companies like FedEx, Nissan, Honda, National Health Service (NHS), etc. During this attack period, WannaCry was temporarily neutralized. The main attempt of attack is to demand a large amount of wealth. The attackers demanded $300 to $600 worth of bitcoin. It was the most expensive cyberattack ever.
Attackers also declare that if the victims do not pay this amount of ransom within 3 days then the attackers will permanently delete the crucial files. Few countries believe and suspect that North Korea can be responsible for this cyberattack.
However, the day after this initial attack Microsoft banned previous security updates for end-of-life products, such as Windows XP, Windows Server 2003, and Windows 8. After this attack, Microsoft updated its security level and became aware of not to happen this unexpected situation again.
#9. Cyberattack on Sony PlayStation Gaming System in 2011
The Sony PlayStation gaming system is a popular product around the world. Unfortunately in 2011, the Sony PlayStation network went down. In that case, approximately 77 million users were prevented from accessing the PlayStation. It does not end here, user credit card data was also encrypted. It is well known and one of the world top 10 cyber security threats.
However, Sony claims that users' information was not encrypted during the intrusion. This outage lasted for 23 days. Sony believes and expresses through a press conference about the weak security system. After that, Sony announced it would invest $170 million to investigate and make their security system very strong.
#10. Melissa Virus Attack on Microsoft in 1999
Melissa virus is a type of email virus. It was created in March 1999. It is a mass mailing virus. It was created to target Microsoft Word and Outlook-based systems. Melissa virus is the fastest spreading virus for risk and potential system damage. The Melissa virus is sent to the user's computer as an email with an important term. If the user clicks on that then the user falls in the trap and is affected by this virus.
It was mostly affected in Microsoft Word 97 and Word 2000. Indeed, this virus would slow down Microsoft Outlook and Microsoft Exchange servers with email. During this attack, many organizations were affected (those who used Microsoft Word and Outlook-based systems). However, on 1st April 1999, David L. Smith (discoverer of the Melissa virus) was arrested in New Jersey by the FBI.
#11. Yahoo Cyberattack in 2014
Internet Service Company Yahoo cyberattack was conducted in 2014 to steal the Yahoo user database. This is because there are more than 500 million user accounts there. It was a famous cyber attack in 2014. Through this attack, cybercriminals grab the user's personal information, such as name, email address, contact number, birth date, hashed passwords, and other details. But how Yahoo was a victim of cybercriminals?
In that case, the hackers sent spear-phishing emails to the Yahoo company employees. It is noted that how many employees were targeted is not clear yet. But if one person clicks on this phishing email then the attacker can control the entire system.
Yahoo was a victim in this way. The major intent of the attackers is to steal Yahoo data. After that Yahoo recruited a new security and technology specialist to update their security system to save them from such brutal attacks.
#12. Adobe Cyberattack in 2013
Adobe is a well-known and leading software company in the world. They have some specific and popular products Adobe Photoshop, Acrobat Reader are familiar around the world. In 2013 Adobe was a victim of cyberattack. In October 2013, Adobe disclosed that hackers had accessed approximately 38 million active users or customer IDs, encrypted passwords, and payment card information.
The attackers stole the source code for several Adobe products, including Adobe Acrobat, ColdFusion, and ColdFusion Builder. The breach occurred through a vulnerability in Adobe's network by unauthorized access to sensitive data. It can be the best-suited for the cyberattack for the next few years. After that, Adobe invested a million dollars to strengthen their security level to avoid unauthorized access to their secret place.
How to Prevent Cyber Security Threats?
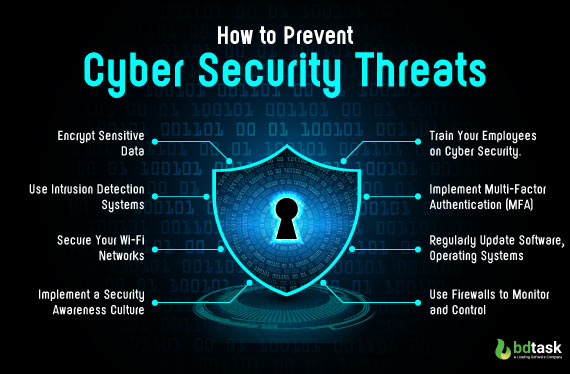
Cybercrime has been a common threat in the digital era. Indeed, this threat will enhance with updating technological expansion. But how to avoid a cyberattack? With those things some key safe ways have been invented also. You may contact a renowned cyber security company that can sufficiently help you to save your business from such a brutal attack.
However, during this modern era, there are some crucial awareness or steps that can perfectly prevent cybercrime. So, let’s see what things you should adopt to protect yourself or how to protect yourself from cyberattack.
- Train your employees on cyber security.
- Implement multi-factor authentication (MFA) to add an extra layer of security passwords.
- Regularly update software, operating systems, and firmware.
- Use firewalls to monitor and control incoming and outgoing network traffic, and use antivirus software to detect and remove malware.
- Encrypt sensitive data both in transit and at rest to protect it from unauthorized interference.
- Use intrusion detection systems, security information, and event management (SIEM) tools to monitor systems to indicate a cyber threat.
- Secure your Wi-Fi networks with strong encryption and unique passwords.
- Implement a Security Awareness Culture within your organization's employees.
It is noted that to make your business secure and more reliable, you may hire a cybersecurity specialist. On the other hand, there are many organizations that offer comprehensive cyber security service. You may get help from them by having a discussion.
Which Five Industries Are Most Vulnerable To Cybercrime?
Cyberattack can be conducted on any company or organization where internet connection is available. Those who conduct cybercrime on any organization must have intention to snatch money, steal data, down the business growth, and others. However, we have found 5 crucial industries where notorious cybercrime can be conducted.
- Healthcare industry
- Financial Industry
- Government Agencies
- Energy and Utility Companies
- Manufacturing Industries
Final Thought
Hacking means some unauthorized person will get access and can snatch data without your help. Can you imagine that your storing data is transferred to others? No one wants to face that situation. That’s why the importance of cybersecurity in the digital age is immeasurable. Cyber terrorism has become more popular due to unprecedented attacks. I have referred to some of the biggest cyberattack in history. People also got shocked whenever such giant companies were hacked. However, there are a bunch of ways to protect your data from unauthorized access.
Disclaimer: I have used a numbering system for victim companies or organizations by some authentic sources. It is noted that this numbering system can fluctuate. In that case, we will never be responsible for that.











